
The recent cyberattacks on critical U.S. infrastructure – Solar Winds, Colonial Pipeline, JBS Meat Packing, to name a few – have brought to the public’s attention the enormous threat posed to our businesses and industries by ransomware attacks. The fact that these attacks can have such a devastating impact on the economy and society is a sobering thought indeed.
But rather than cower in fear, I think it’s important, make that imperative, that everyone in the world of IT understand the nature of these attacks and rigorously follow best practices to prevent their businesses from being taken hostage by ransomware criminals. The challenge is enormous, but with knowledge, perseverance, and action, we can blunt the threat.
First of all, what is ransomware and how does it work?
Ransomware is a type of malware that threatens to publish the victim’s personal data or perpetually block access to it unless a ransom is paid. While some ransomware may not be difficult for a knowledgeable person to reverse, more advanced malware uses a technique called cryptoviral extortion that encrypts the victim’s files, making them inaccessible. Only after the ransom is paid (often in difficult to trace Bitcoin) will the criminals provide the decryption key. Recovering the files without the decryption key is extremely difficult, if not practically impossible.
Ransomware attacks are typically carried out using a Trojan Horse approach in which a network user is tricked into downloading or opening a malware file that arrives as a legitimate looking email attachment. Upon entering the victim’s network, the malware may lay dormant for a long period of time while it provides the criminals with a window into system activity. That activity can lead to a compromise of the server password.
Once one machine gets compromised, the attacker may hide for up to 90 days to monitor activity, learn the landscape, and capture passwords. Then the attacker activates encryption for all known files like .docx, .xlsx, .pdf, .jpg etc. The encryption occurs on all local drives as well as network drives (folder shares on server) that are mapped. There’s also the possibility the attacker logs in directly to the server and does the same. Victims are usually made aware of the problem when they log in one day and see a screen like this, indicating that file extensions have changed and are no longer readable.
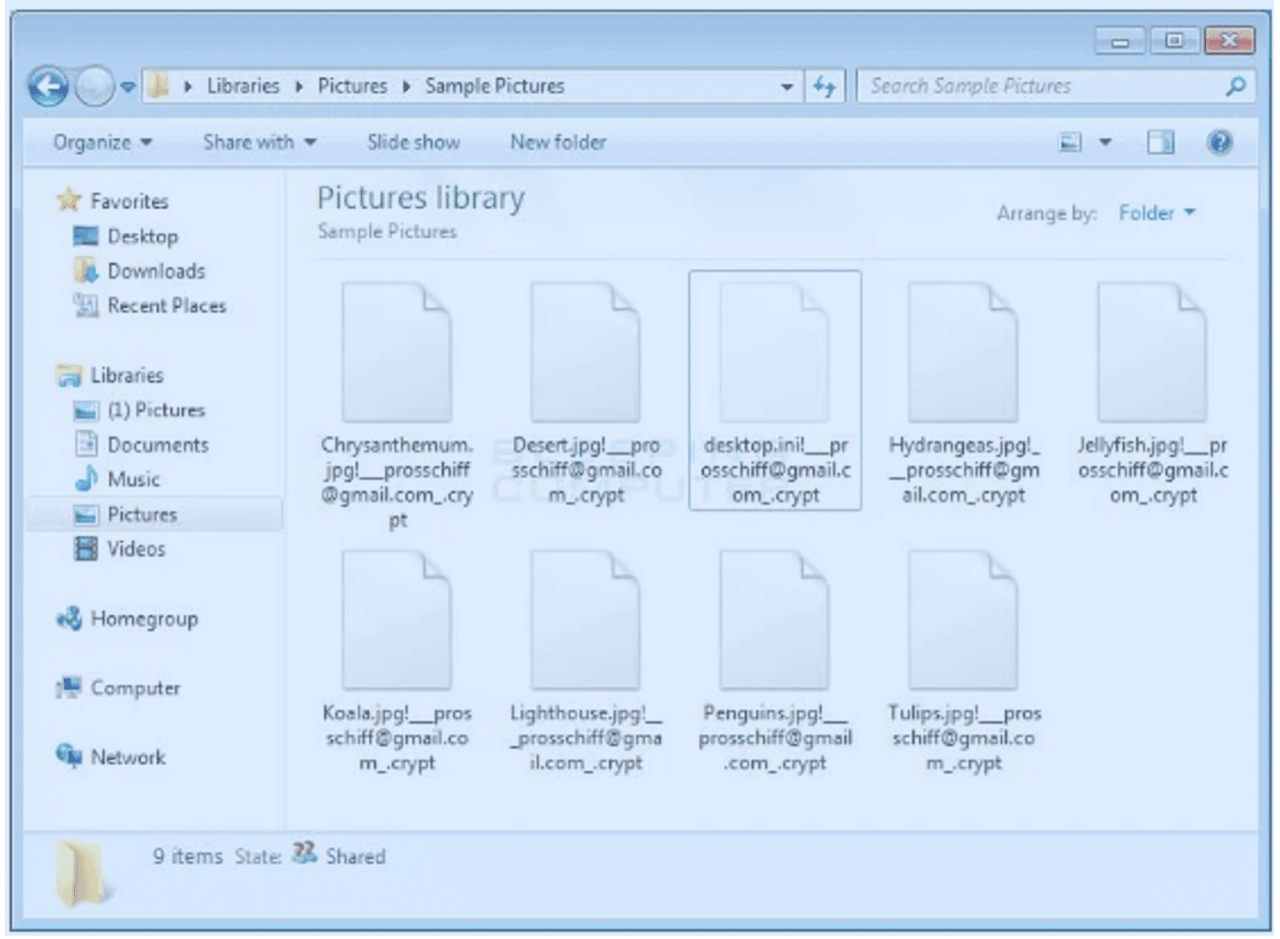
The objective of most ransomware attacks is to hijack sensitive information and threaten its public disclosure or destruction unless the ransom is paid, often within a few days’ time. In the past few years, 95% of victimized organizations that paid the ransom had their data restored. Criminals are generally interested in getting the money and disappearing, not taking over and running someone’s IT network.
Starting from around 2012, ransomware attacks have grown exponentially. In June 2014, cybersecurity vendor McAfee released data showing that it had collected more than double the number of ransomware samples that quarter than it had in the same quarter of 2013. More recently, there were 181.5 million ransomware attacks in the first six months of 2018, marking a 229% increase over the number of attacks in 2017.

In 2020, the International Crime Complaint Center received over 2,400 complaints identified as ransomware, with losses totalling over $29 million. And these were just the losses publicly reported. The FBI has estimated that total losses, many unreported, were likely substantially more. In that same year, software security vendor Sophos found that the global average cost to remediate a ransomware attack (considering downtime, people time, device cost, network cost, lost opportunity and ransom paid) was $761,000. And right now, the REvil hackers behind the ransomware attack on Kaseya are demanding an exorbitant $70 million in ransom.
These are just a few of the sobering statistics. I could go on but you get the idea: ransomware, like other forms of scams and cyber terrorism, is a fact of life that’s here to stay, and an enormous problem for us all.
So that’s a high-level overview of the threat. In my next blog, I’ll cover some of the best practices that any business can follow to protect themselves from ransomware attacks and largely negate the efforts of greedy and ruthless cyber criminals.

